security monitoring to identify and respond to threats effectively.
For proactive security monitoring and observability with Bigtecsys, you can utilize dedicated security dashboards and advanced analytics to identify and respond to threats effectively
- Access a dedicated dashboard specifically designed for monitoring security.
- Monitor security metrics and alerts in real-time to stay ahead of potential threats.
Gain visibility into security events across networks, infrastructures, applications, and databases.
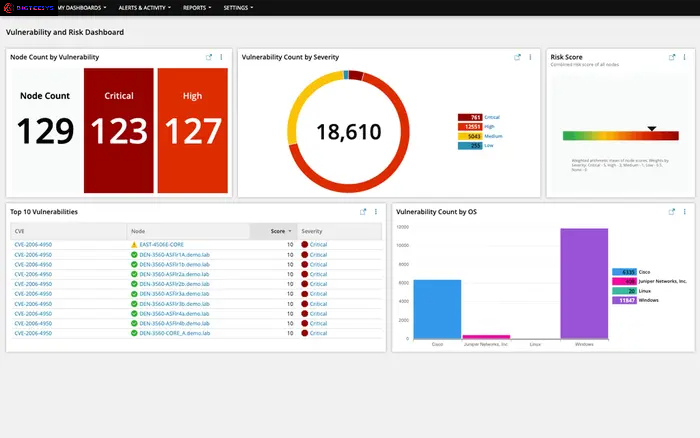
Vulnerability and risk dashboard
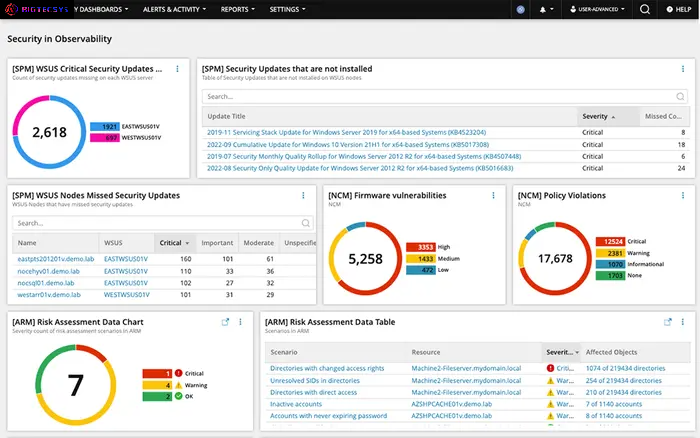
Bigtecsys introduces its latest Vulnerability and Risk Dashboard, designed to empower customers in identifying and mitigating risks based on vulnerabilities across a variety of devices and platforms
Comprehensive Device Coverage: CSupported Devices: Monitor vulnerabilities across Cisco, Juniper, Windows, Linux, and VMware devices.
Unified Dashboard: Centralized View: Access a single dashboard to view and manage vulnerabilities across all supported devices.
Risk Identification and Assessment: Risk Mapping: Map vulnerabilities to potential risks and assess their impact on business operations.
Real-time Alerts and Notifications: Alerting Mechanisms: Receive real-time alerts and notifications for newly discovered vulnerabilities or changes in risk status.
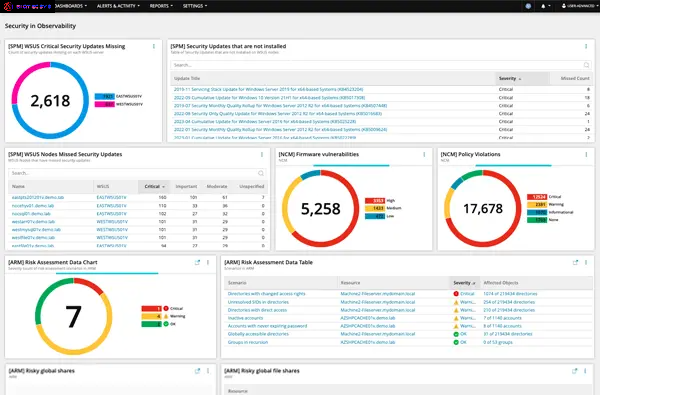
Security summary dashboard
Bigtecsys' Security Summary Dashboard solution provides a comprehensive view of security events across various IT domains, integrating data from Security Event Manager (SEM), Access Rights Manager (ARM), and Patch Manager.
Unified Visibility: Single Dashboard: Access a unified view of security events across networks, infrastructures, applications, and databases.
Integrated Summary Widgets: Event Monitoring: Monitor and analyze security events in real-time.
Real-Time Monitoring: Live Updates: Monitor security events and incidents in real-time to promptly respond to threats.
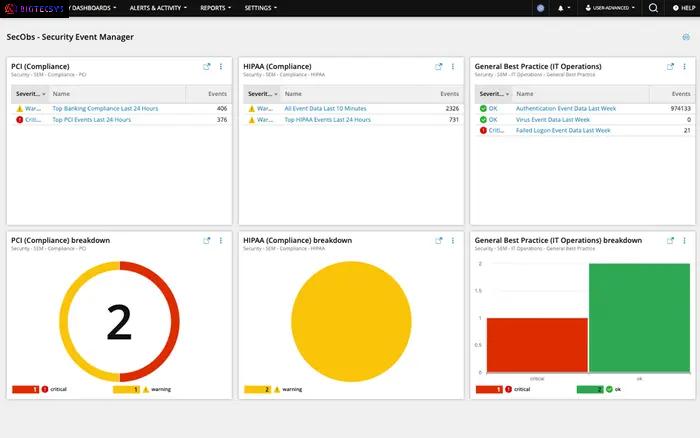
SEM summary dashboard
The SEM (Security Event Manager) Summary Dashboard in Bigtecsys offers powerful capabilities for monitoring security events based on saved queries.
Widget-based Display: Custom Widgets: Display widgets based on SEM-saved queries. Visualization: Visualize key security metrics and insights derived from SEM query results.
Scheduled Execution: Automated Execution: Schedule SEM queries to run at specified intervals (e.g., hourly, daily).
Threshold Management: Threshold Settings: Define minimum or maximum thresholds for query results.
Customization and Flexibility: Configurable Dashboards: Customize dashboards with widgets that reflect specific security metrics and insights.
Security Monitoring and Observability
Ensure the resilience of your organization's digital assets with Bigtecsys's advanced Security Monitoring and Observability solutions. Our comprehensive platform empowers you to proactively detect, analyze, and respond to security threats across your entire IT environment. With a focus on real-time visibility and actionable insights, Bigtecsys equips your team with the tools needed to safeguard critical systems and data effectively.
Real-Time Threat Detection: Monitor your network, applications, and infrastructure in real-time to identify suspicious activities and potential security breaches as they occur.
Customizable Alerts: Set up alerts and notifications based on predefined rules and thresholds to promptly respond to security incidents and mitigate risks.

Security Monitoring and Observability
Successful cloud migration can transform your organization by offering numerous benefits. Bigtecsys provides tools to benchmark and optimize the performance of on-premises workloads before and after migration, ensuring a smooth and efficient transition
Hybrid Cloud Observability
Self-hosted observability to take you from reactive to proactive across on-prem and hybrid IT environments.
- Deployment to meet your needs, whether behind your firewall or self-hosted in AWS®, Microsoft® Azure, or GCP®
- Flexible licensing – allocate nodes across multiple instances – and optimal scalability
- Built from our years of network management leadership and enhanced with machine learning
Access Rights Manager
Manage and audit access rights across your IT infrastructure
- Rapidly identify and reduce the risk of unauthorized system access and data breaches
- Easily create user accounts and review user permissions, groups, and access across all systems and data
- Help demonstrate compliance with reports
Security Event Manager
Improve your security posture and quickly demonstrate compliance with an easy-to-use, affordable SIEM tool
- Centralized log collection and retention
- Automated threat detection response
- Integrated compliance reporting tool
- Enhanced Security Posture
- Cost-Effective Solution
Let's Try! Get Free Support
Start Your 6-Day Free Trial
From security to observability and beyond, Bigtecsys helps you go from visibility to action.